Automated ISO 27001 & SOC 2 compliance for fast-growing startups
Within 30 days, Smartly collects, organizes, and prepares data for your audit. Pay only after you are certified!
Get certified nowTrusted by companies worldwide












Don't let compliance drain your resources for building and selling
Outsource your end-to-end compliance and certification journey to Smartly, so you can focus on running your business while we manage the heavy lifting.
01
Kick-off
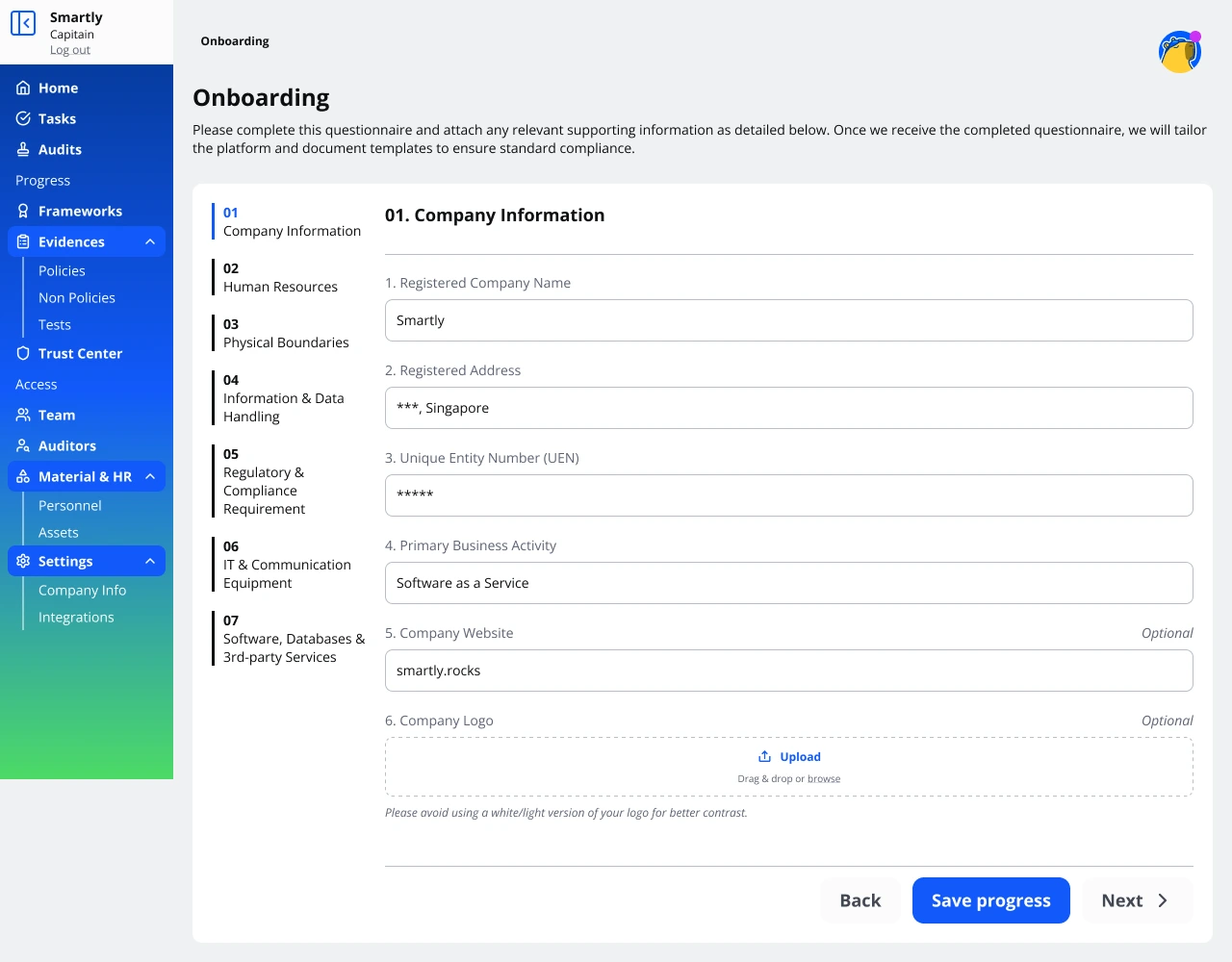
Define Scope, Risk Assessment & Gap Analysis
- Start by answering simple questionnaire - no technical jargon, just straightforward organizational information.
- Get your risk assessments, gap analysis, and action to-do lists, saving you time and effort.
of compliance tasks automated
control checks mapped
days to get compliant
We handle compliance so you can build trust and sell to enterprise clients
Built by Compliance Experts
We're ISO 27001 certified ourselves, and we have automated it so you can get certified with less effort than we did.
Effortless Automation
Smartly takes care of 70% of manual compliance tasks, from documentation to evidence collection, saving you weeks of stress.
24/7 Customer Support
Questions, blockers, or audits coming up? Our support team is available 24/7 to guide you every step of the way.
Made for Startups
Designed for startups with lean budgets, Smartly delivers fast compliance at a fraction of the usual price, no consultants or hidden fees.
Which compliance framework is right for you?
Early
Secure new deals, validate market fit, and reach the milestones you need to unlock funding.
Hyper Growth
Enter - and win - new markets with a security compliance program that adapts to your changing needs.
Late-stage
Drive efficiency in your security program and reduce risk with better visibility into your people, vendors, and assets.

Free ISO 27001 & SOC 2 Checklists for Startups
Explore our step-by-step guidance and timeline for your audit preparation
Free ISO 27001 Preparation Checklist
Get our comprehensive preparation checklist with actionable steps to guide you through your ISO 27001 certification journey, made for startups and SMEs.
By submitting, I agree to Smartly’s Privacy Policy.

Your Complete Path to ISO 27001 Certification
A structured 90-day plan that takes startups and fast-growing teams from zero to audit-ready. Follow the Plan-Do-Check-Act approach aligned with ISO 27001:2022 framework.
By submitting, I agree to Smartly’s Privacy Policy.

Your Complete Path to SOC 2 Certification
A comprehensive SOC 2 preparation checklist that show you what to do: from planning through audit readiness. Follow the Plan-Do-Check-Act approach aligned with Trust Services Criteria.
By submitting, I agree to Smartly’s Privacy Policy.
Here are what our clients love about Smartly

"Before Smartly, we found doing ISO 27001 really complicated, trying to make sense of all the requirements, documentation and what we needed to do. Now it is super easy and quick, as we know exactly what to do, saving weeks of time. Our audit preparation has been a breeze since."

"What stood out most to me was how approachable the Smartly team is. Whenever we had a question, they responded quickly with clear answers and solutions. We always felt supported and assured when preparing for our audit."

"The best part has been the customer service. Anytime I got stuck, someone from Smartly hopped on a call and walked me through it. They were patient with my questions and felt like part of my team."
Smartly vs. Vanta: Which Is Best for Your ISO 27001 Compliance?
Discover why Smartly is faster, more affordable, and better suited for APAC startups seeking ISO 27001 certification.
Read Full ComparisonTime to certification compared to traditional consultancies
Average savings vs traditional compliance solutions
Automation that actually works, not just marketing talk
Trusted by startups and SMEs across Southeast Asia
Resources
Our events, expert insights and practical guides for your compliance journey
Ready to cut audit prep by 80%?
Streamline your ISO 27001 journey and build trust with Smartly today!







